Set Up Microsoft Entra ID App Registration
Table of Contents:
Set Up Microsoft Entra ID App Registration
Microsoft Entra ID (formerly Azure Active Directory) is used to create OAuth applications for organization‑wide access in Microsoft 365. This guide walks you through registering an application, assigning Microsoft Graph permissions, and authenticating using client credentials.
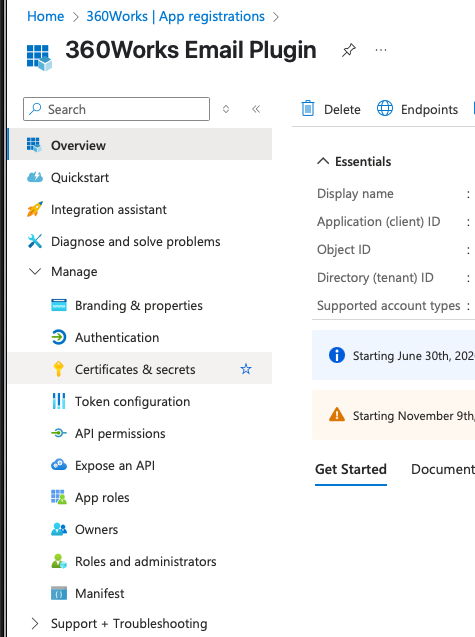
Register Your App in Entra ID
- Go to the Azure Portal.
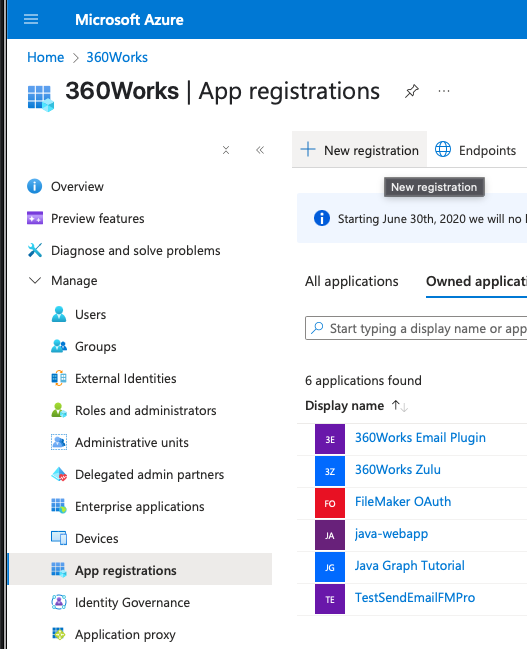
- Navigate to Microsoft Entra ID
- Navigate to App registrations.
- Click + New registration.
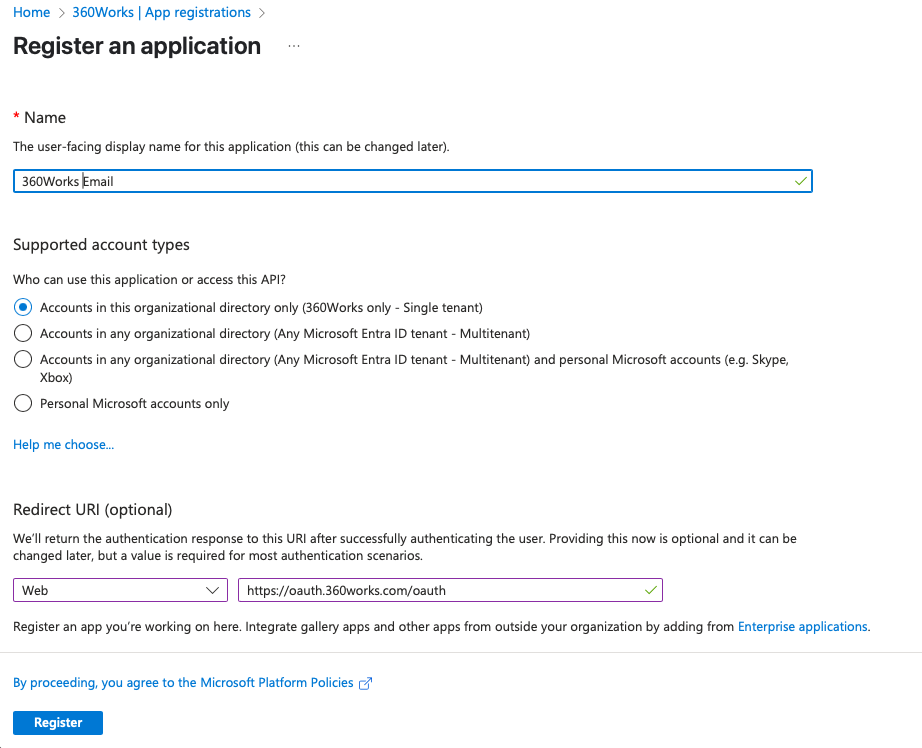
- Fill in:
- Name - e.g.
360Works Email - Supported account types - Accounts in this organizational directory only (Single tenant)
- Redirect URI → Web:
https://oauth.360works.com/oauth
- Name - e.g.
- Click Register.
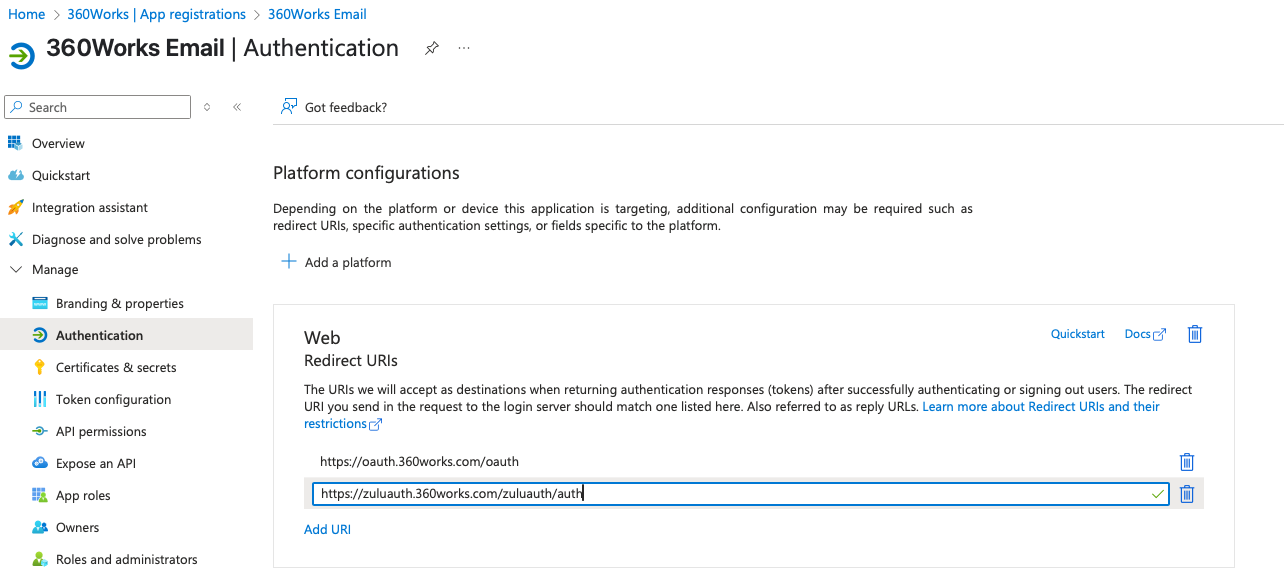
- Add the second Redirect URI (same page → Right Side Under the URI listing):
https://zuluauth.360works.com/zuluauth/auth
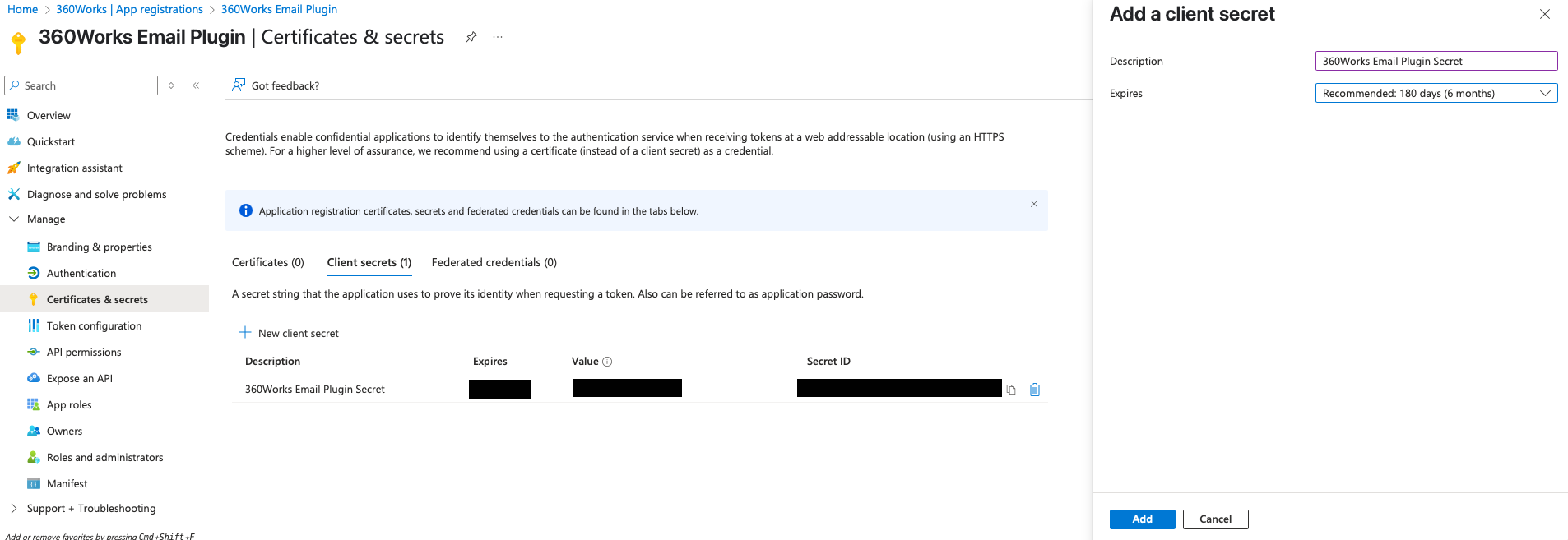
Create a Client Secret
- In your app, open Certificates & secrets.
- Click + New client secret.
- Enter a description and select an expiration (maximum 24 months).
- Click Add and copy the secret value (you won’t see it again).
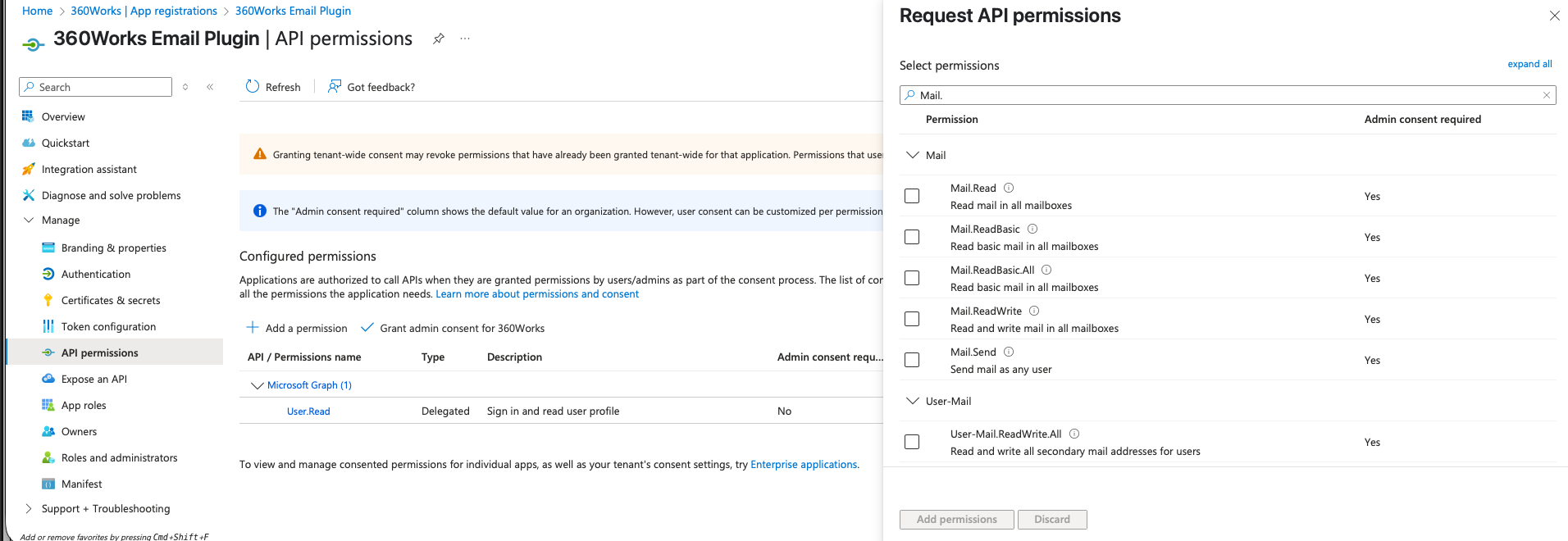
Assign Microsoft Graph API Permissions
- Open API permissions.
- Click + Add a permission → Microsoft Graph → Application permissions.
- Search Mail and add:
Mail.ReadWriteMail.Send
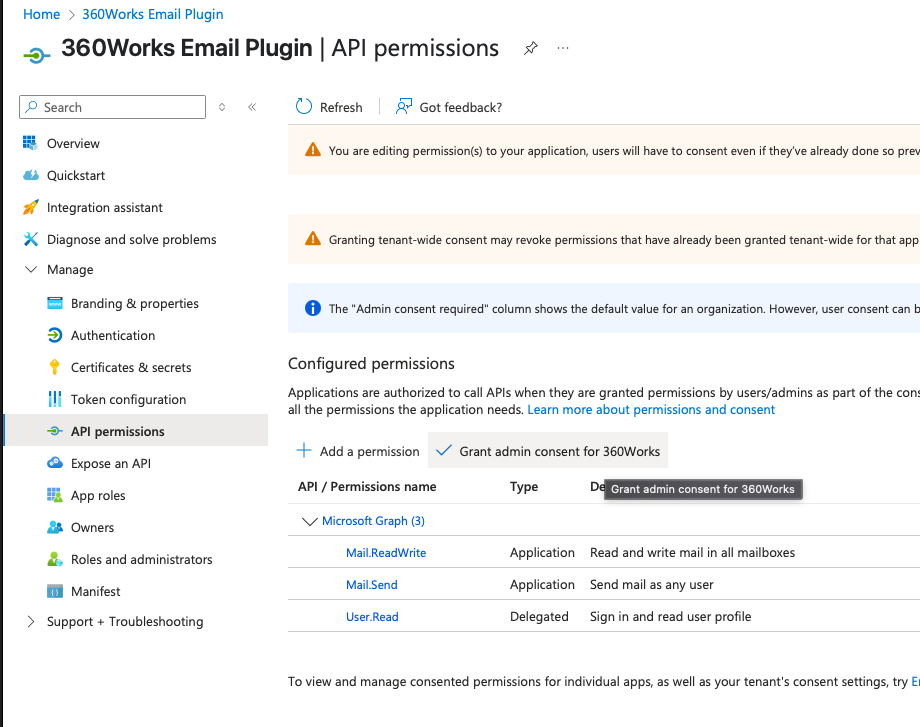
- Click Grant admin consent (Global Administrator required).
This setup allows your app to read, send, and delete mail across the organization with no per-user consent required.